In an period the place data is essentially the most invaluable asset, it’s important for organizations to have robust controls over who can entry delicate knowledge and sources.Position Primarily based Entry Management (RBAC) is among the handiest approaches in reaching this objective.
By way of this text, you’ll discover the ideaPosition Primarily based Entry Management in depth and its necessary parts. Let’s begin with a primary understanding of what RBAC is!
10 Benefits of Learning Programming You Need to Know
What’s Position Primarily based Entry Management?

Position Primarily based Entry Management (RBAC), or Position Primarily based Entry Management, is an strategy utilized in data safety administration to manage and handle person or entity entry rights inside a system or group.
In RBAC, entry to varied sources and capabilities within the system is set by the roles held by these people or entities. Which means that customers or entities are granted permissions or entry rights based mostly on the roles or obligations they assume throughout the context of a specific group or system.
RBAC permits system managers to prepare entry in a extra structured and environment friendly method, making it simpler to observe and handle entry rights, and decreasing the chance of unauthorized or unauthorized entry.
With this idea, organizations can be certain that every particular person or entity solely has entry to the knowledge or sources essential to finish their duties or obligations, thereby bettering total system safety and manageability.
Konsep RBAC (Position Primarily based Entry Management)
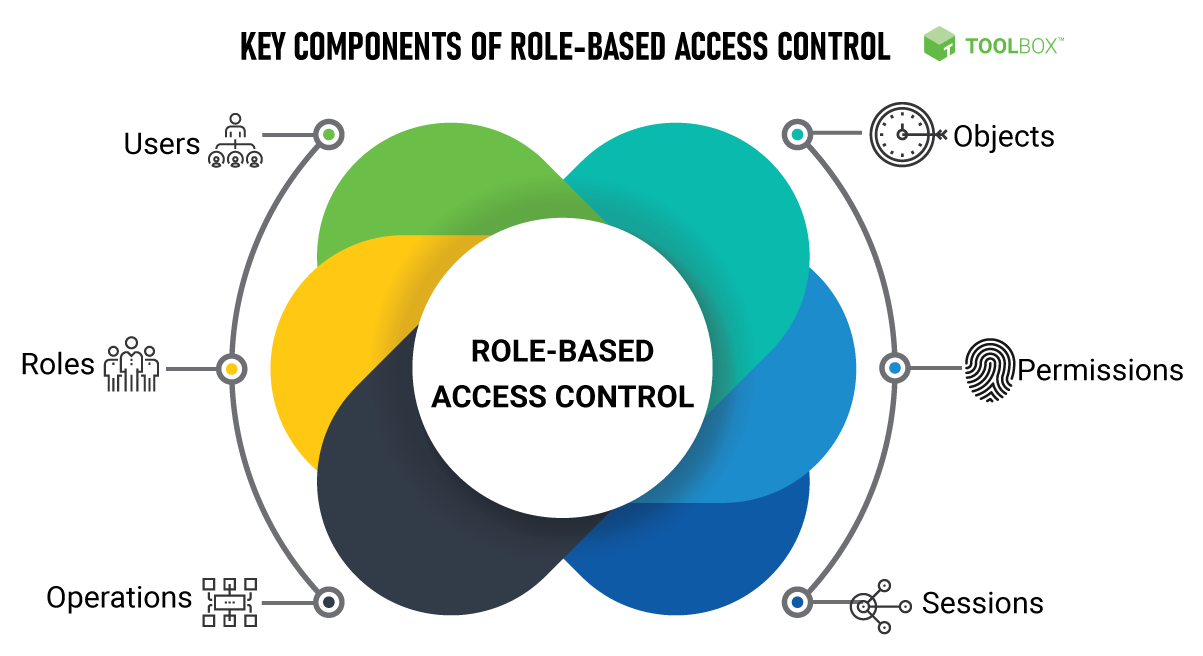
RBAC idea (Position Primarily based Entry Management) is an entry management strategy that prioritizes the usage of roles as the idea for granting permissions, which simplifies the administration course of considerably. In RBAC, there are three major ideas which might be generally used, specifically:
1. Person Position Project
This precept determines person permissions or entry rights based mostly on the roles or duties they’ve within the group or system. When a person adjustments place or if they’re now not related to a company, directors can simply change their function, and permissions will mechanically replace. RBAC permits customers to be assigned to a number of roles directly, which supplies flexibility in entry administration.
2. Person Position Authorization
This precept ensures {that a} person is permitted to imagine a task and carry out associated capabilities. Which means that not all customers have entry to all roles. For instance, a person could also be permitted to be an “Administrator”, however not have permission to be an “Worker”.
3. Person Position Permission and Entry Rights
This precept clearly defines what a person can and can’t do based mostly on their function. This permission covers points corresponding to:
- Entry: This precept determines which customers can open sure objects, corresponding to information, purposes, or databases. As well as, it’s also essential to contemplate who ought to know in regards to the existence of sure belongings and the restrictions that apply relating to visibility.
- Modification: This precept regulates which customers could make adjustments to sure objects. As well as, it additionally explains what approval is required to make adjustments.
- Sharing: This precept identifies customers who can obtain paperwork and customers who can share paperwork with different customers.
In RBAC, it is very important keep in mind that permissions comply with roles, not the opposite method round. That’s, first decide what every function ought to do, after which apply permissions based on these roles. In figuring out RBAC permissions, rigorously take into account who can entry what and what they’ll do within the system. This can assist enhance safety and scale back the chance of unauthorized entry inside your group or methods.
What is Mariadb? Definition and Main Functions
Komponen Position Base Entry Management
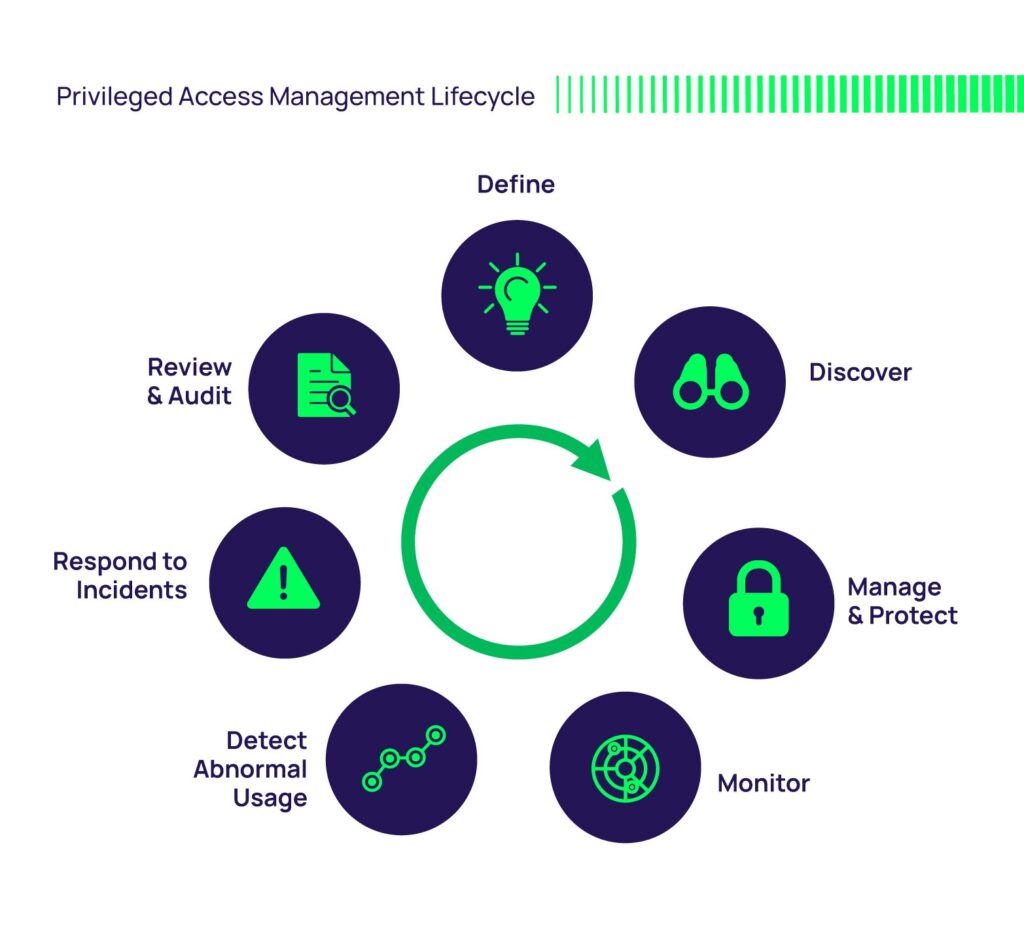
Position Primarily based Entry Management (RBAC) is a posh entry management system, and to grasp how RBAC capabilities, it is very important perceive its necessary parts. Following are the 5 major parts of RBAC:
1. Routing
Routing in RBAC determines how entry requests from customers are routed to the suitable system. This is a crucial first step within the entry management course of.Routing Environment friendly methods be certain that entry requests get to the suitable place rapidly and securely.
2. Permission
Permission refers back to the entry rights granted to every function within the system. These permissions particularly outline what actions the function holder can carry out. For instance, permission to learn, write, or delete knowledge. Permissions are the inspiration of RBAC as a result of they outline what every function can do within the system.
3. Position
Position are entities or capabilities supplied to customers or entities in RBAC. Every function has an outlined set of permissions or entry rights. For instance, the “Administrator” function could have completely different permissions than the “Common Person” function. Roles describe the duties or obligations performed by a person or entity in a company or system.
4. Entry Project
Entry Project is the method of assigning roles to customers or entities within the system. This task of entry have to be carried out rigorously and in accordance with the duties or obligations of the person or entity. For instance, a brand new worker could also be assigned the “Worker” function which supplies entry permissions acceptable to their job.
5. Guidelines
Guidelines in RBAC are tips that regulate how permissions are granted and managed. These guidelines could differ relying on the safety coverage of the group or system. They assist in defining procedures for managing adjustments in roles, permissions, and entry assignments.
Tipe Position Primarily based Entry Management

Position Primarily based Entry Management (RBAC) is a really versatile strategy, and there are a number of varieties of RBAC that may be carried out based on organizational or system wants. The 4 major varieties of RBAC are:
1. Core RBAC
Core RBAC is essentially the most primary kind of RBAC. On this kind, roles and permissions are assigned in a comparatively easy method. Every person normally solely has one function. It is a appropriate strategy for organizations that require a primary degree of entry management.
2. Hierarchical RBAC
In kindHierarchical RBAC, roles are grouped in a hierarchical construction. This implies that there’s a relationship between greater roles and decrease roles. Larger roles normally have larger permissions than decrease roles. This kind is appropriate for organizations with a posh hierarchical construction.
3. Symmetric RBAC
Symmetric RBAC permits customers to have a couple of function. Every function has distinctive permissions. This supplies larger flexibility in managing entry, as customers can have varied roles that replicate their completely different roles within the group or system.
4. Constrained RBAC
SortConstrained RBAC imposes stricter restrictions on customers when it comes to the variety of permissions they’ve. It’s utilized in conditions the place very strict entry controls are required, corresponding to in excessive safety or strict regulatory environments.
With an understanding ofPosition Primarily based Entry Management (RBAC) that we mentioned above, it is very important keep in mind that an excellent RBAC implementation can enhance system safety and scale back the chance of unauthorized entry. In an effort to implement RBAC extra successfully in your group, we extremely suggest contemplating utilizing the serviceCloud Product Indonesia from Cloudera.